Encryption- mixing up, distorting or changing of data being transmitted over a network to prevent unauthorized disclosure.
A password – a secret code used to prevent unauthorized access of data in a computer
Kavungya answered the question on June 5, 2019 at 10:15
- Draw a labeled diagram to illustrate the internal structure of a diskette.(Solved)
Draw a labeled diagram to illustrate the internal structure of a diskette.
Date posted: June 5, 2019. Answers (1)
- Give two differences between post Office Mail electronic mail ( E- mail)(Solved)
Give two differences between post Office Mail electronic mail ( E- mail)
Date posted: June 5, 2019. Answers (1)
- Speed and accuracy are some of the advantages of using computers in banking. State three other advantages of using computers in banking.(Solved)
Speed and accuracy are some of the advantages of using computers in banking. State three other advantages of using computers in banking.
Date posted: June 5, 2019. Answers (1)
- What happens when the following commands are typed in the DOS environment?
(i) CD
(ii) Dir(Solved)
What happens when the following commands are typed in the DOS environment?
(i) CD
(ii) Dir
Date posted: June 5, 2019. Answers (1)
- In DOS, what are the following commands used for?
(i) RD
(ii) DEL(Solved)
In DOS, what are the following commands used for?
(i) RD
(ii) DEL
Date posted: June 5, 2019. Answers (1)
- List three parts that constitute an array definition statement(Solved)
List three parts that constitute an array definition statement
Date posted: June 5, 2019. Answers (1)
- With the improvement in price and performance of computers and communication equipment it will be possible for people in various business organizations to work from...(Solved)
With the improvement in price and performance of computers and communication equipment it will be possible for people in various business organizations to work from home. Such working using a PC as a remote terminal is often described as teleworking. State three advantages and three disadvantages of working from home.
Date posted: June 5, 2019. Answers (1)
- Bidii wholesalers has two categories of customers for order processing, category ‘A’ obtains 10% discount on all orders up to Kshs 10,000 otherwise the discount...(Solved)
Bidii wholesalers has two categories of customers for order processing, category ‘A’ obtains 10% discount on all orders up to Kshs 10,000 otherwise the discount is 20% on the entire order. Category “B’ obtains 30% discount on all orders if the debt repayment is ‘good’ otherwise the discount is 15%. Draw a flowchart for the order processing
Date posted: June 5, 2019. Answers (1)
- Explain three ways by which computer users can protect their eyes from harmful emissions from the computer screen(Solved)
Explain three ways by which computer users can protect their eyes from harmful emissions from the computer screen
Date posted: June 5, 2019. Answers (1)
- A school bought a computer system. The hardware items supplied include: a 800 MHz processor, 64 MB of RAM, a sound card, speakers, a monitor,...(Solved)
A school bought a computer system. The hardware items supplied include: a 800 MHz processor, 64 MB of RAM, a sound card, speakers, a monitor, a keyboard, a 120 GB hard disk, a floppy disk drive, a CD – Read/ write drive, a mouse, a modem, an inkjet printer and a joystick.
The software supplied include: an operating system, a BASIC interpreter and the following packages: spreadsheets, graphics, word processor, art, database and games
(a) List three input devices from the given specifications
(b) Explain the meaning of the following
(i) 800 MHZ
(ii) 64 MB of RAM
(iii) 120 GB hard disk
(c) Some of the students in the school use the computer to do homework. Name the package used to:
(i) Do calculations and draw graphs
(ii) Write an essay
(iii) Make a poster
(d) Students enjoy playing noisy computer games
(i) Which two hardware items are needed to produce sound?
(ii) Which input device is only used for playing games?
Date posted: June 5, 2019. Answers (1)
- A school organizes its work in directories. The director WP contains the files CATS, EXAMS and ASSIGNMENTS. The directory of SP contain the spreadsheet files....(Solved)
A school organizes its work in directories. The director WP contains the files CATS, EXAMS and ASSIGNMENTS. The directory of SP contain the spreadsheet files. The directory DB contains the database files. The directory PROG is contained in the OTHERS directory. The directory WP also contains the PERSONAL directory. Given that the directory STUDENT contains directories SP, DB, WP and OTHERS
(a) Draw the directory tree structure with C as the root
(b) Write the path at which the contents of subdirectory DB can be erased or displayed
Date posted: June 5, 2019. Answers (1)
- Write the path for the directory PROG(Solved)
Write the path for the directory PROG
Date posted: June 5, 2019. Answers (1)
- Give two reasons for storing files in directories and subdirectories(Solved)
Give two reasons for storing files in directories and subdirectories
Date posted: June 5, 2019. Answers (1)
- Give two disadvantages of using command driven interfaces as compared to menu driven interfaces(Solved)
Give two disadvantages of using command driven interfaces as compared to menu driven interfaces
Date posted: June 5, 2019. Answers (1)
- Indicate whether the following devices are used for input or output
(i) Plotter
(ii) Light pen
(iii) mouse
(iv) Visual display unit(Solved)
Indicate whether the following devices are used for input or output
(i) Plotter
(ii) Light pen
(iii) mouse
(iv) Visual display unit
Date posted: June 5, 2019. Answers (1)
- Explain why the following controls should be implemented for computer based systems
(i) Back- ups
(ii) Password(Solved)
Explain why the following controls should be implemented for computer based systems
(i) Back- ups
(ii) Password
Date posted: June 5, 2019. Answers (1)
- For each of the following give one reason why they are not allowed in a computer laboratory
(i) Smoking
(ii) Eating foods(Solved)
For each of the following give one reason why they are not allowed in a computer laboratory
(i) Smoking
(ii) Eating foods
Date posted: June 5, 2019. Answers (1)
- The cells K3 to K10 of a worksheet contain remarks on students ’ performance such as very good, good, fair and fail depending on the...(Solved)
The cells K3 to K10 of a worksheet contain remarks on students ’ performance such as very good, good, fair and fail depending on the average mark. Write a formula that can be used to count ALL students who have the remark “very good”.
Date posted: June 5, 2019. Answers (1)
- A serial file comprises of records placed in positions 1 to 10. State the position of the end of the file market.(Solved)
A serial file comprises of records placed in positions 1 to 10. State the position of the end of the file market.
Date posted: June 5, 2019. Answers (1)
- Name the control structure depicted by the flowchart below(Solved)
Name the control structure depicted by the flowchart below
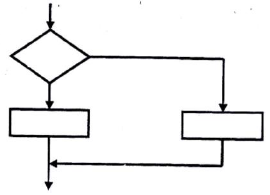
Date posted: June 5, 2019. Answers (1)