- Threats to the safety of computer systems take many forms such as: Whitecollar
crime, natural, disasters, vandalism and carelessness.
- Give one way as to how each...(Solved)
Threats to the safety of computer systems take many forms such as: Whitecollar
crime, natural, disasters, vandalism and carelessness.
- Give one way as to how each of these forms of threats can be controlled
Date posted: June 25, 2019. Answers (1)
- Give four differences between present days’ computers and the older generation of computers(Solved)
Give four differences between present days’ computers and the older generation of computers
Date posted: June 25, 2019. Answers (1)
- State and explain two precautions that be taken to help recover data lost through accidental erasure(Solved)
State and explain two precautions that be taken to help recover data lost through accidental erasure
Date posted: June 25, 2019. Answers (1)
- The following flowchart can be used to list the odd numbers between 0 and
100
(a) Write a program segment for the flowchart using a high level...(Solved)
The following flowchart can be used to list the odd numbers between 0 and
100
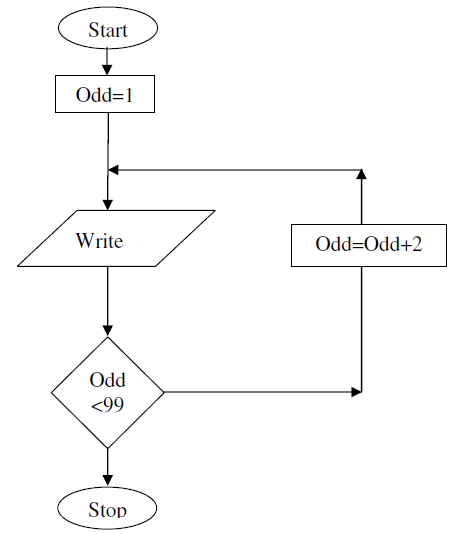
(a) Write a program segment for the flowchart using a high level language
(b) What would be the output from the flowchart if the statement in the decision
box is changed to:
(c) Modify the flowchart so that it prints only the sum of the odd numbers
between o and 100
Date posted: June 25, 2019. Answers (1)
- Write – 1 in two's compliment notation in byte form(Solved)
Write – 1 in two's compliment notation in byte form
Date posted: June 25, 2019. Answers (1)
- State and explain two reasons why word processing is one of the most common applications of many computer users.(Solved)
State and explain two reasons why word processing is one of the most common applications of many computer users.
Date posted: June 25, 2019. Answers (1)
- List three differences between a microcomputer and a super – computer(Solved)
List three differences between a microcomputer and a super – computer
Date posted: June 25, 2019. Answers (1)
- Give one disadvantages of a single processor multi- user system.(Solved)
Give one disadvantages of a single processor multi- user system.
Date posted: June 25, 2019. Answers (1)
- The Formula = k20 + p $18 was typed in cell L21 and then copied to cell M24
of a spreadsheet. Write the formula as it...(Solved)
The Formula = k20 + p $18 was typed in cell L21 and then copied to cell M24
of a spreadsheet. Write the formula as it appears in cell M24
Date posted: June 25, 2019. Answers (1)
- State any three activities that occur in a program compilation process(Solved)
State any three activities that occur in a program compilation process
Date posted: June 25, 2019. Answers (1)
- Suppose an element array A contains the values 9, 12, 17, 7 and 20. Find the
value in A after executing the loop below:
Repeat for k=...(Solved)
Suppose an element array A contains the values 9, 12, 17, 7 and 20. Find the
value in A after executing the loop below:
Repeat for k= 1 to 4
Set A {k + 1} = A {k}
{End of loop}
Date posted: June 25, 2019. Answers (1)
- Distinguish between “serial” and “indexed sequential” file organization methods(Solved)
Distinguish between “serial” and “indexed sequential” file organization methods
Date posted: June 25, 2019. Answers (1)
- The diagram below represents the essential features of a computer
system. Study the diagram and answer the questions that follow:
(a) Name the components: A B C...(Solved)
The diagram below represents the essential features of a computer
system. Study the diagram and answer the questions that follow:
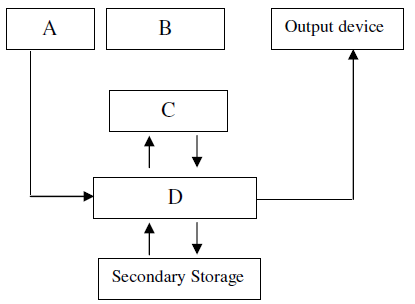
(a) Name the components: A B C D
(b) Name the three types of buses in a computer system
(c) Explain how the CPU registers may be used to carry out a basic calculation
such as 2 + 7 = 9
(d) Name two computers output devices
Date posted: June 25, 2019. Answers (1)
- A program is required to list the first 1000 numbers in the series 2, 4, 6, 8, 10 ……. Draw a flowchart and write a...(Solved)
A program is required to list the first 1000 numbers in the series 2, 4, 6, 8, 10 ……. Draw a flowchart and write a program that can be carry out this task
Date posted: June 25, 2019. Answers (1)
- Define a Pseudo code.(Solved)
Define a Pseudo code.
Date posted: June 25, 2019. Answers (1)
- Name two DOS commands that may be used for checking disk errors(Solved)
Name two DOS commands that may be used for checking disk errors
Date posted: June 25, 2019. Answers (1)
- Give one difference between internal and external commands in Disk Operating System(Solved)
Give one difference between internal and external commands in Disk Operating System
Date posted: June 25, 2019. Answers (1)
- Define the term application Software.(Solved)
Define the term application Software.
Date posted: June 25, 2019. Answers (1)
- List any four tasks that an electronic spreadsheet should be able to perform other than calculations.(Solved)
List any four tasks that an electronic spreadsheet should be able to perform other than calculations.
Date posted: June 25, 2019. Answers (1)
- The first column in the table below contains the formulae as stored into the
cell F10 of a spreadsheet. Enter the formulae, as they would appear...(Solved)
The first column in the table below contains the formulae as stored into the
cell F10 of a spreadsheet. Enter the formulae, as they would appear when
copied to the cell M20 of the same spreadsheet.
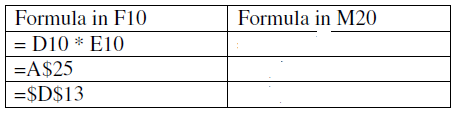
Date posted: June 25, 2019. Answers (1)