(i)
-Redundancy
-Inadequate storage for data
-Data security threats
-Slow access rate of data
(ii)
-Interviews
-Questionnaire
-Observation
-Studying available existing documentation
-Automated methods
(iii)
-Corrective maintenance
-Preventive maintenance
-Adaptive maintenance
-Perfective maintenance
maurice.mutuku answered the question on August 20, 2019 at 08:57
- Differentiate between testing and debugging as used in programming.(Solved)
Differentiate between testing and debugging as used in programming.
Date posted: August 20, 2019. Answers (1)
- Draw a flow chart that counts all the even numbers between 1 and 20 inclusive and then displays the sum which uses a repeat loop.(Solved)
Draw a flow chart that counts all the even numbers between 1 and 20 inclusive and then displays the sum which uses a repeat loop.
Date posted: August 20, 2019. Answers (1)
- Mwanaisha deposited Ksh 10000 in a bank at an interest rate of 20% per annum. At the end of each year, the interest earned is...(Solved)
Mwanaisha deposited Ksh 10000 in a bank at an interest rate of 20% per annum. At the end of each year, the interest earned is added to the deposit and the new amount becomes the deposit of that year.
Write a pseudo code that would track the growth of the deposit over a period of 5 years.
Date posted: August 20, 2019. Answers (1)
- Differentiate between hot swapping and plug and play as used in computing.(Solved)
Differentiate between hot swapping and plug and play as used in computing.
Date posted: August 20, 2019. Answers (1)
- Use figures below to answers the questions that follow.(Solved)
Use figures below to answers the questions that follow.
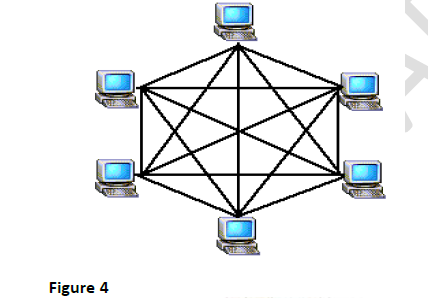
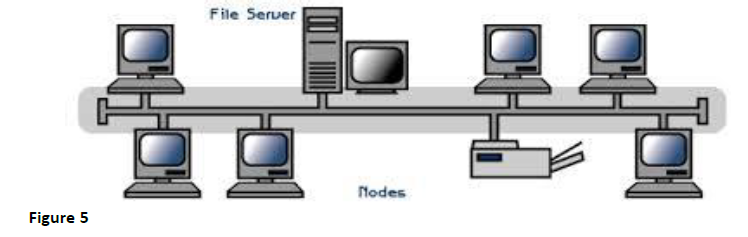
(i) Identify the network topologies in Figure 4 and Figure 5 above.
(ii) Explain why it is beneficial to use the topology in Figure 4 above.
Date posted: August 20, 2019. Answers (1)
- The following worksheet represents the number of stems of various types of flowers exported in Ken Flower Ltd.(Solved)
The following worksheet represents the number of stems of various types of flowers exported in Ken Flower Ltd.
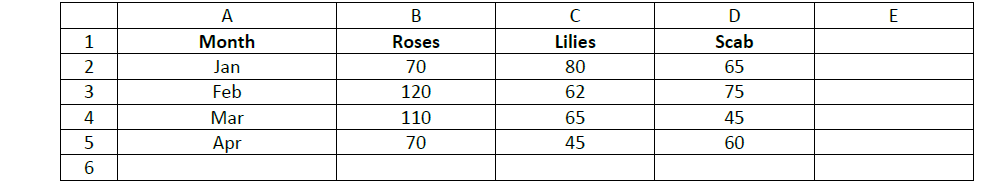
The cost of each stem from the farmer is Kshs 25. This amount is typed in cell B10.
(a) Write a function that will calculate the total number of stems of all the types of flowers in all months.
(b) Write a formula that can be typed in cell E2 and then be copied down to obtain monthly purchases for Roses.
(c) Identify the data type in cell C1 and cell D3.
Date posted: August 20, 2019. Answers (1)
- Figure 3 below shows a removable storage media. Use it to answer the questions that follow.(Solved)
Figure 3 below shows a removable storage media. Use it to answer the questions that follow.
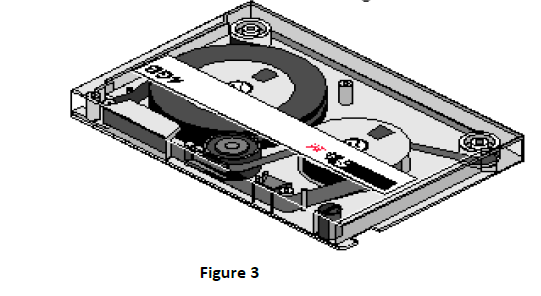
a) Identify the storage media above.
b) Explain two disadvantages of using the storage media above.
Date posted: August 20, 2019. Answers (1)
- Differentiate between working storage and auxiliary storage .(Solved)
Differentiate between working storage and auxiliary storage .
Date posted: August 20, 2019. Answers (1)
- The following computer components were displayed to inform computer students during a practical lesson.(Solved)
The following computer component were displayed to inform computer students during a practical lesson.
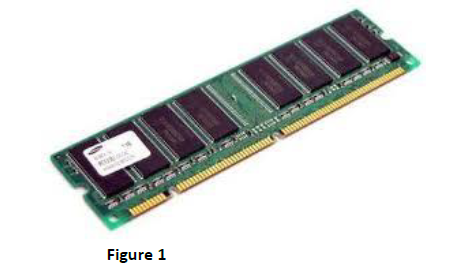

a) Identify the components in Figure 1 and Figure 2 above.
Figure 1-
Figure 2-
b) Explain how each of the components identified influences on the capability of a computer.
Date posted: August 20, 2019. Answers (1)
- Differentiate between merging cells and splitting cell in a table when using word processors.(Solved)
Differentiate between merging cells and splitting cell in a table when using word processors.
Date posted: August 20, 2019. Answers (1)
- Give examples of database systems(Solved)
Give examples of database systems
Date posted: August 2, 2019. Answers (1)
- What is a Flowchart?(Solved)
What is a Flowchart?
Date posted: August 2, 2019. Answers (1)
- State three objectives of normalization(Solved)
State three objectives of normalization
Date posted: August 2, 2019. Answers (1)
- Define normalization(Solved)
Define normalization
Date posted: August 2, 2019. Answers (1)
- Explain the difference between data privacy and data security.(Solved)
Explain the difference between data privacy and data security.
Date posted: August 2, 2019. Answers (1)
- Briefly explain the following terms:
(Solved)
Briefly explain the following terms:
i) Label
ii) Value
iii) function
Date posted: August 2, 2019. Answers (1)
- Explain the difference between a system software and application programs.(Solved)
Explain the difference between a system software and application programs.
Date posted: August 2, 2019. Answers (1)
- Outline the steps to be followed in order to merge cells in a word processing table.(Solved)
Outline the steps to be followed in order to merge cells in a word processing table.
Date posted: June 25, 2019. Answers (1)
- Distinguish between Mouse pointer and insertion point.(Solved)
Distinguish between Mouse pointer and insertion point.
Date posted: June 25, 2019. Answers (1)
- Distinguish between a table in word-processing application and a table in a database application(Solved)
Distinguish between a table in word-processing application and a table in a database application
Date posted: June 25, 2019. Answers (1)