(i) When the analyst wants to collect confidential information.
(ii) When there is a large group of people involved in the system.
(iii) When the people you want to gather information from are vastly dispersed.
maurice.mutuku answered the question on September 27, 2019 at 06:14
- A student presented a budget in the form of a worksheet as follows.(Solved)
A student presented a budget in the form of a worksheet as follows.
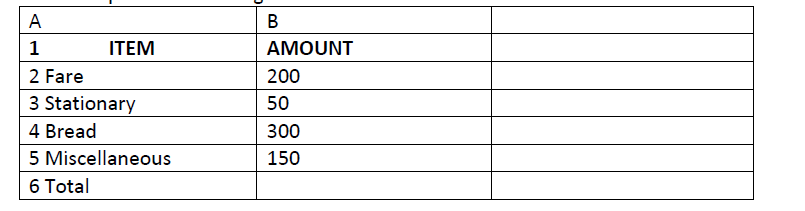
a) Write a formula to get the total in B6
b) State the expression that would be used to obtain the least expenditure.
Date posted: September 27, 2019. Answers (1)
- State three factors that you would consider before replacing or upgrading a computer memory(Solved)
State three factors that you would consider before replacing or upgrading a computer memory
Date posted: September 27, 2019. Answers (1)
- Mobile phones have becomes common ICT devices. List some of the powerful capabilities that come with some of the latest embedded operating systems in mobile...(Solved)
Mobile phones have becomes common ICT devices. List some of the powerful capabilities that come with some of the latest embedded operating systems in mobile phones.
Date posted: September 27, 2019. Answers (1)
- Convert the following into binary
i) 76CD16
ii) 1238 (Solved)
Convert the following into binary
i) 76CD16
ii) 1238
Date posted: September 27, 2019. Answers (1)
- List four types as courses in ICT offered at degree level in Kenya.(Solved)
List four types as courses in ICT offered at degree level in Kenya.
Date posted: September 27, 2019. Answers (1)
- State three factors that have led to slow growth of e-learning in Kenyan schools.(Solved)
State three factors that have led to slow growth of e-learning in Kenyan schools.
Date posted: September 27, 2019. Answers (1)
- Explain the difference between ring and star network topology.(Solved)
Explain the difference between ring and star network topology.
Date posted: September 27, 2019. Answers (1)
- Define the following terms
i). Spam mail
ii). Disk(Solved)
Define the following terms
i). Spam mail
ii). Disk
Date posted: September 27, 2019. Answers (1)
- Masai Teacher’s college has decided to automate its library for effective services to the Students. Identify four methods they are likely to use to gather...(Solved)
Masai Teacher’s college has decided to automate its library for effective services to the Students. Identify four methods they are likely to use to gather information during system development.
Date posted: September 26, 2019. Answers (1)
- Outline four major ways the company network administrator can enforce good network practice on user of the company LAN.(Solved)
Outline four major ways the company network administrator can enforce good network practice on user of the company LAN.
Date posted: September 26, 2019. Answers (1)
- Explain the following terms as used in the word processing
a). indenting
b). Foot note
c). Endnote(Solved)
Explain the following terms as used in the word processing
a). indenting
b). Foot note
c). Endnote
Date posted: September 26, 2019. Answers (1)
- Give Two features of neural networks.(Solved)
Give Two features of neural networks.
Date posted: September 26, 2019. Answers (1)
- Information and Communication Technology is relatively a new area of study which is advancing. Due to this reason, everyone is expected to keep a breast...(Solved)
Information and Communication Technology is relatively a new area of study which is advancing. Due to this reason, everyone is expected to keep a breast with the changing trend of information and Communication Technology (ICT).
Explain how ICT has affected employment
Date posted: September 26, 2019. Answers (1)
- Why are CD-ROM and CD-R referred to as WORM?(Solved)
Why are CD-ROM and CD-R referred to as WORM?
Date posted: September 26, 2019. Answers (1)
- Study the diagram below and answer the questions that follow.(Solved)
Study the diagram below and answer the questions that follow.
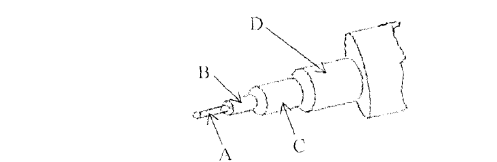
(i) Name the above cable as used in data communication media
(ii) Name the parts labeled A, B, C and D
(iii) Highlight any Three advantages of the above cable.
Date posted: September 26, 2019. Answers (1)
- Computer hardware is categorized according to the types of operations it performs. List Three operations.(Solved)
Computer hardware is categorized according to the types of operations it performs. List Three operations.
Date posted: September 26, 2019. Answers (1)
- State any Three advantages of simulation in training(Solved)
State any Three advantages of simulation in training
Date posted: September 26, 2019. Answers (1)
- List Four E-mail services(Solved)
List Four E-mail services
Date posted: September 26, 2019. Answers (1)
- Differentiate between real time processing and batch processing giving examples where each could be used(Solved)
Differentiate between real time processing and batch processing giving examples where each could be used
Date posted: September 26, 2019. Answers (1)
- Give Two possible ways of fitting the document in one page(Solved)
Give Two possible ways of fitting the document in one page
Date posted: September 26, 2019. Answers (1)