
-Public domain. This is the most permissive type of software license. When software is in the public domain, anyone can modify and use the software without any restrictions. But you should always make sure it’s secure before adding it to your own codebase. Warning: Code that doesn’t have an explicit license is NOT automatically in the public domain. This includes code snippets you find on the internet.
-Permissive. Permissive licenses are also known as “Apache style” or “BSD style.” They contain minimal requirements about how the software can be modified or redistributed. This type of software license is perhaps the most popular license used with free and open source software. Aside from the Apache License and the BSD License, another common variant is the MIT License.
LGPL. The GNU Lesser General Public License allows you to link to open source libraries in your software. If you simply compile or link an LGPL-licensed library with your own code, you can release your application under any license you want, even a proprietary license. But if you modify the library or copy parts of it into your code, you’ll have to release your application under similar terms as the LGPL.
-Copyleft. Copyleft licenses are also known as reciprocal licenses or restrictive licenses. The most well-known example of a copyleft or reciprocal license is the GPL. These licenses allow you to modify the licensed code and distribute new works based on it, as long as you distribute any new works or adaptations under the same software license. For example, a component’s license might say the work is free to use and distribute for personal use only. So any derivative you create would also be limited to personal use only. (A derivative is any new software you develop that contains the component.)
The catch here is that the users of your software would also have the right to modify the code. Therefore, you’d have to make your own source code available. But of course, exposing your source code may not be in your best interests.
-Proprietary. Of all types of software licenses, this is the most restrictive. The idea behind it is that all rights are reserved. It’s generally used for proprietary software where the work may not be modified or redistributed.
Titany answered the question on November 30, 2021 at 08:28
- Figure 1 shows an Ethernet frame. Outline the parts labelled(Solved)
Figure 1 shows an Ethernet frame. Outline the parts labelled
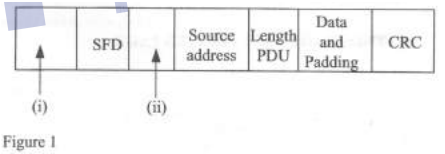
Date posted: November 30, 2021. Answers (1)
- Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks(Solved)
Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks
Date posted: November 30, 2021. Answers (1)
- Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend(Solved)
Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend
Date posted: November 30, 2021. Answers (1)
- Distinguish between channel B and channel D as used in integrated services digital network (ISDN)(Solved)
Distinguish between channel B and channel D as used in integrated services digital network (ISDN)
Date posted: November 30, 2021. Answers (1)
- Outline two applications of a CSMA/CD technology(Solved)
Outline two applications of a CSMA/CD technology
Date posted: November 30, 2021. Answers (1)
- Describe two classification of fiber optic cables(Solved)
Describe two classification of fiber optic cables
Date posted: November 30, 2021. Answers (1)
- TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol...(Solved)
TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol that promotes its reliable transport
Date posted: November 30, 2021. Answers (1)
- Explain three functions of data link layer(Solved)
Explain three functions of data link layer
Date posted: November 30, 2021. Answers (1)
- Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols(Solved)
Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between symmetric and asymmetric keys as used in network security(Solved)
Differentiate between symmetric and asymmetric keys as used in network security
Date posted: November 30, 2021. Answers (1)
- A good network design should produce a scalable network. Outline four ways of achieving this network objective(Solved)
A good network design should produce a scalable network. Outline four ways of achieving this network objective
Date posted: November 30, 2021. Answers (1)
- Explain three Internet services that could be utilized by students in technical institutions
(Solved)
Explain three Internet services that could be utilized by students in technical institutions
Date posted: November 30, 2021. Answers (1)
- Convert the digital encoded signal in (i) into on-return-to-zero (NRZ) line code(Solved)
Convert the digital encoded signal in (i) into on-return-to-zero (NRZ) line code
Date posted: November 30, 2021. Answers (1)
- With the aid of a diagram, represent the data 10110001 in the form of a digital
encoded wave form
(Solved)
With the aid of a diagram, represent the data 10110001 in the form of a digital
encoded wave form
Date posted: November 30, 2021. Answers (1)
- Distinguish between broadcast and host IP addresses(Solved)
Distinguish between broadcast and host IP addresses
Date posted: November 30, 2021. Answers (1)
- Outline two advantages of point to point protocol (PPP)(Solved)
Outline two advantages of point to point protocol (PPP)
Date posted: November 30, 2021. Answers (1)
- Discuss different types of computer networks (Solved)
Discuss different types of computer networks
Date posted: November 30, 2021. Answers (1)
- Explain two characteristics of a local area network (Solved)
Explain two characteristics of a local area network
Date posted: November 30, 2021. Answers (1)
- With the aid of examples, describe two categories of wireless networks that could be found in organizations(Solved)
With the aid of examples, describe two categories of wireless networks that could be found in organizations
Date posted: November 30, 2021. Answers (1)
- Use of passwords promotes network security. Outline four precautions that should be considered when assigning passwords(Solved)
Use of passwords promotes network security. Outline four precautions that should be considered when assigning passwords
Date posted: November 30, 2021. Answers (1)