
The mail system has two major parts : MTAs and UAs. A message transfer agent (MTA) routes a mail message towards its final destination by sending the message to another MTA. A user agent (UA) interacts with an end-user and allows the user to send and receive mail messages.
On the Internet, MTAs communicate with each other using the Simple Mail Transfer Protocol (SMTP). SMTP follows the client/ server model of computing. The SMTP client initiates the dialogue with an SMTP server by sending a message to the remote server. This message includes the following information : the sender address, the recipient address (maybe more than one), and the message itself.
Another useful mail protocol is Post Office Protocol (POP). With POP one can set up a machine as a mail drop point. POP lets a userís mailbox reside on a remote host, but allows the user to retrieve the messages from the remote mailbox on demand. As such, POP is user driven, since mail is not transferred until the user requests that be done. After the transfer, the user can read mail on the local system whenever itís convenient. Replies are relayed to the POP server using SMTP. There are two versions of POP -- POP2 and POP3.
The SMTP protocol suffers from one significant defect : it understands only 7-bit ASCII characters. Consequently, you canít use SMTP to send binary data such as graphics or programs. Multipurpose Internet Mail Extensions (MIME) provides a standard by specifying a set of encoding rules and header extensions to the Internet standard message specification. These rules let a UA encode messages with text, graphics, and even sound into 7-bit ASCII.
Titany answered the question on November 30, 2021 at 08:33
- Describe two modes of licensing for network software(Solved)
Describe two modes of licensing for network software
Date posted: November 30, 2021. Answers (1)
- Figure 1 shows an Ethernet frame. Outline the parts labelled(Solved)
Figure 1 shows an Ethernet frame. Outline the parts labelled
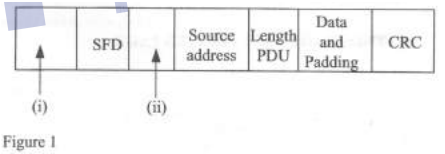
Date posted: November 30, 2021. Answers (1)
- Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks(Solved)
Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks
Date posted: November 30, 2021. Answers (1)
- Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend(Solved)
Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend
Date posted: November 30, 2021. Answers (1)
- Distinguish between channel B and channel D as used in integrated services digital network (ISDN)(Solved)
Distinguish between channel B and channel D as used in integrated services digital network (ISDN)
Date posted: November 30, 2021. Answers (1)
- Outline two applications of a CSMA/CD technology(Solved)
Outline two applications of a CSMA/CD technology
Date posted: November 30, 2021. Answers (1)
- Describe two classification of fiber optic cables(Solved)
Describe two classification of fiber optic cables
Date posted: November 30, 2021. Answers (1)
- TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol...(Solved)
TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol that promotes its reliable transport
Date posted: November 30, 2021. Answers (1)
- Explain three functions of data link layer(Solved)
Explain three functions of data link layer
Date posted: November 30, 2021. Answers (1)
- Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols(Solved)
Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between symmetric and asymmetric keys as used in network security(Solved)
Differentiate between symmetric and asymmetric keys as used in network security
Date posted: November 30, 2021. Answers (1)
- A good network design should produce a scalable network. Outline four ways of achieving this network objective(Solved)
A good network design should produce a scalable network. Outline four ways of achieving this network objective
Date posted: November 30, 2021. Answers (1)
- Explain three Internet services that could be utilized by students in technical institutions
(Solved)
Explain three Internet services that could be utilized by students in technical institutions
Date posted: November 30, 2021. Answers (1)
- Convert the digital encoded signal in (i) into on-return-to-zero (NRZ) line code(Solved)
Convert the digital encoded signal in (i) into on-return-to-zero (NRZ) line code
Date posted: November 30, 2021. Answers (1)
- With the aid of a diagram, represent the data 10110001 in the form of a digital
encoded wave form
(Solved)
With the aid of a diagram, represent the data 10110001 in the form of a digital
encoded wave form
Date posted: November 30, 2021. Answers (1)
- Distinguish between broadcast and host IP addresses(Solved)
Distinguish between broadcast and host IP addresses
Date posted: November 30, 2021. Answers (1)
- Outline two advantages of point to point protocol (PPP)(Solved)
Outline two advantages of point to point protocol (PPP)
Date posted: November 30, 2021. Answers (1)
- Discuss different types of computer networks (Solved)
Discuss different types of computer networks
Date posted: November 30, 2021. Answers (1)
- Explain two characteristics of a local area network (Solved)
Explain two characteristics of a local area network
Date posted: November 30, 2021. Answers (1)
- With the aid of examples, describe two categories of wireless networks that could be found in organizations(Solved)
With the aid of examples, describe two categories of wireless networks that could be found in organizations
Date posted: November 30, 2021. Answers (1)