1. Delivery:
The system must deliver data to the correct destination. Data must be received by the intended device or user and only by that device or user.
2. Accuracy:
The system must deliver the data accurately. Data that have been altered in transmission and left uncorrected are unusable.
3. Timeliness:
The system must deliver data in a timely manner. Data delivered late are useless. In the case of video and audio, timely delivery means delivering data as they are produced, in the same order that they are produced, and without significant delay. This kind of delivery is called real-time transmission.
4. Jitter:
Jitter refers to the variation in the packet arrival time. It is the uneven delay in the delivery of audio or video packets. For example, let us assume that video packets are sent every 3D ms. If some of the packets arrive with 3D-ms delay and others with 4D-ms delay, an uneven quality in the video is the result.
Titany answered the question on November 30, 2021 at 08:39
- Define the term node as applied in data transmission(Solved)
Define the term node as applied in data transmission
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
(Solved)
Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
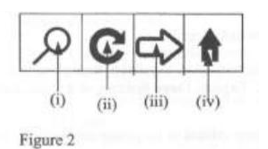
Date posted: November 30, 2021. Answers (1)
- Outline four roles of user agent as used in email software(Solved)
Outline four roles of user agent as used in email software
Date posted: November 30, 2021. Answers (1)
- Describe two modes of licensing for network software(Solved)
Describe two modes of licensing for network software
Date posted: November 30, 2021. Answers (1)
- Figure 1 shows an Ethernet frame. Outline the parts labelled(Solved)
Figure 1 shows an Ethernet frame. Outline the parts labelled
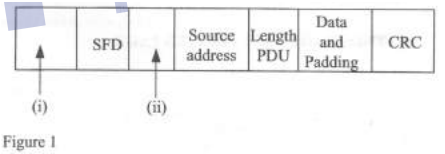
Date posted: November 30, 2021. Answers (1)
- Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks(Solved)
Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks
Date posted: November 30, 2021. Answers (1)
- Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend(Solved)
Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend
Date posted: November 30, 2021. Answers (1)
- Distinguish between channel B and channel D as used in integrated services digital network (ISDN)(Solved)
Distinguish between channel B and channel D as used in integrated services digital network (ISDN)
Date posted: November 30, 2021. Answers (1)
- Outline two applications of a CSMA/CD technology(Solved)
Outline two applications of a CSMA/CD technology
Date posted: November 30, 2021. Answers (1)
- Describe two classification of fiber optic cables(Solved)
Describe two classification of fiber optic cables
Date posted: November 30, 2021. Answers (1)
- TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol...(Solved)
TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol that promotes its reliable transport
Date posted: November 30, 2021. Answers (1)
- Explain three functions of data link layer(Solved)
Explain three functions of data link layer
Date posted: November 30, 2021. Answers (1)
- Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols(Solved)
Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between symmetric and asymmetric keys as used in network security(Solved)
Differentiate between symmetric and asymmetric keys as used in network security
Date posted: November 30, 2021. Answers (1)
- A good network design should produce a scalable network. Outline four ways of achieving this network objective(Solved)
A good network design should produce a scalable network. Outline four ways of achieving this network objective
Date posted: November 30, 2021. Answers (1)
- Explain three Internet services that could be utilized by students in technical institutions
(Solved)
Explain three Internet services that could be utilized by students in technical institutions
Date posted: November 30, 2021. Answers (1)
- Convert the digital encoded signal in (i) into on-return-to-zero (NRZ) line code(Solved)
Convert the digital encoded signal in (i) into on-return-to-zero (NRZ) line code
Date posted: November 30, 2021. Answers (1)
- With the aid of a diagram, represent the data 10110001 in the form of a digital
encoded wave form
(Solved)
With the aid of a diagram, represent the data 10110001 in the form of a digital
encoded wave form
Date posted: November 30, 2021. Answers (1)
- Distinguish between broadcast and host IP addresses(Solved)
Distinguish between broadcast and host IP addresses
Date posted: November 30, 2021. Answers (1)
- Outline two advantages of point to point protocol (PPP)(Solved)
Outline two advantages of point to point protocol (PPP)
Date posted: November 30, 2021. Answers (1)