
• Signal damping is a common phenomenon that is overcome via regeneration and retransmission of the data signals done by these devices.
• To ensure successful transfers these devices keep record of information of source address, destination address or different pathways existing through the network depending upon the switching technique being employed.
• They also detect faults and errors effectively using redundancy bits, etc. and notify the devices to further ensure fault tolerance by performing corrections while transferring data in a computer network.
• Maintenance of a definite desired flow control and response timeout during the entire course of the communication.
• Setup, grouping and direction of messages (or packets) according to their priorities is done by these devices.
• Provide network security by permitting or denying the flow of data, based on security settings.
Processes running on the intermediary network devices perform these functions:
• regenerate and retransmit data signals
• maintain information about what pathways exist through the network and internetwork
• notify other devices of errors and communication failures
• direct data along alternate pathways when there is a link failure
• classify and direct messages according to quality ofsService (QoS) priorities
• permit or deny the flow of data, based on security settings.
Titany answered the question on November 30, 2021 at 11:17
- Distinguish between intermediary and host devices(Solved)
Distinguish between intermediary and host devices
Date posted: November 30, 2021. Answers (1)
- Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation(Solved)
Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation
Date posted: November 30, 2021. Answers (1)
- Outline two factors that should be considered when selecting an Internet bandwidth, other than cost(Solved)
Outline two factors that should be considered when selecting an Internet bandwidth, other than cost
Date posted: November 30, 2021. Answers (1)
- Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system(Solved)
Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system
Date posted: November 30, 2021. Answers (1)
- Define the term node as applied in data transmission(Solved)
Define the term node as applied in data transmission
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
(Solved)
Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
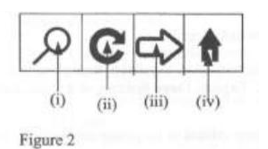
Date posted: November 30, 2021. Answers (1)
- Outline four roles of user agent as used in email software(Solved)
Outline four roles of user agent as used in email software
Date posted: November 30, 2021. Answers (1)
- Describe two modes of licensing for network software(Solved)
Describe two modes of licensing for network software
Date posted: November 30, 2021. Answers (1)
- Figure 1 shows an Ethernet frame. Outline the parts labelled(Solved)
Figure 1 shows an Ethernet frame. Outline the parts labelled
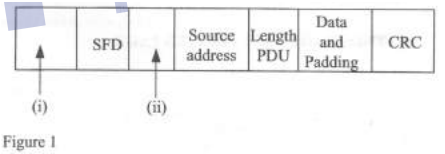
Date posted: November 30, 2021. Answers (1)
- Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks(Solved)
Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks
Date posted: November 30, 2021. Answers (1)
- Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend(Solved)
Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend
Date posted: November 30, 2021. Answers (1)
- Distinguish between channel B and channel D as used in integrated services digital network (ISDN)(Solved)
Distinguish between channel B and channel D as used in integrated services digital network (ISDN)
Date posted: November 30, 2021. Answers (1)
- Outline two applications of a CSMA/CD technology(Solved)
Outline two applications of a CSMA/CD technology
Date posted: November 30, 2021. Answers (1)
- Describe two classification of fiber optic cables(Solved)
Describe two classification of fiber optic cables
Date posted: November 30, 2021. Answers (1)
- TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol...(Solved)
TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol that promotes its reliable transport
Date posted: November 30, 2021. Answers (1)
- Explain three functions of data link layer(Solved)
Explain three functions of data link layer
Date posted: November 30, 2021. Answers (1)
- Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols(Solved)
Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between symmetric and asymmetric keys as used in network security(Solved)
Differentiate between symmetric and asymmetric keys as used in network security
Date posted: November 30, 2021. Answers (1)
- A good network design should produce a scalable network. Outline four ways of achieving this network objective(Solved)
A good network design should produce a scalable network. Outline four ways of achieving this network objective
Date posted: November 30, 2021. Answers (1)
- Explain three Internet services that could be utilized by students in technical institutions
(Solved)
Explain three Internet services that could be utilized by students in technical institutions
Date posted: November 30, 2021. Answers (1)