
1. Misconfiguration
Misconfiguration is the cause of as many as 80% of unplanned outages. Reduce the change of making mistakes by using automation to deploy changes rather than relying on setting parameters manually. Test all configurations in a lab environment before making changes on your production devices.
2. Security breaches
Security failures and allowing unauthorized traffic can bring down a network due to excess load. Make sure you have appropriate security controls in place to keep intruders from overloading your network.
3. Old equipment
Every obsolete, unsupported device is a potential threat to your network’s functioning. Be proactive in planning upgrades and replacing out-of-date equipment.
4. Human error
Perhaps the leading cause of outages are unintentional mistakes. Along with configuration errors, people make mistakes that can be as simple as pulling the wrong plug or not knowing the proper procedure. Avoid these errors through proper staff training and proper documentation, including labels on all devices.
5. Incompatible changes
These aren’t misconfigurations or configuration changes made in error; these problems arise when a change you intend doesn’t work properly alongside your other equipment. Avoid these problems through testing changes and new devices in a lab setting before placing them in production. You’ll also reduce these issues if you have good records of your current devices and settings to help you identify incompatibilities in advance.
6. Hardware failures
Any device can fail; make sure you perform maintenance and apply patches as needed to keep devices up to date and reduce the risk. You can also reduce the impact of any device failure by building in redundancy to prevent a single point of failure from disrupting the whole network.
7. Power failures
Have backup power supplies to prevent a power outage from shutting you down. Connect redundant devices to different power circuits to ensure a single circuit outage doesn’t shut down a service entirely.
You can avoid many of these errors by keeping good records and reducing the amount of manual work your team performs with automation. Monitoring and performing preventative maintenance go a long way to minimizing the risk of equipment failures that bring down your network.
8. Low Bandwidth
If you choose a low bandwidth in the beginning, but your online work increases over time, then your old bandwidth will be unable to handle the new demand and cause a systems slowdown.
Titany answered the question on November 30, 2021 at 11:19
- Outline three factors that should be used when selecting the type of computer network(Solved)
Outline three factors that should be used when selecting the type of computer network
Date posted: November 30, 2021. Answers (1)
- Functions of Intermediary Devices(Solved)
Functions of Intermediary Devices
Date posted: November 30, 2021. Answers (1)
- Distinguish between intermediary and host devices(Solved)
Distinguish between intermediary and host devices
Date posted: November 30, 2021. Answers (1)
- Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation(Solved)
Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation
Date posted: November 30, 2021. Answers (1)
- Outline two factors that should be considered when selecting an Internet bandwidth, other than cost(Solved)
Outline two factors that should be considered when selecting an Internet bandwidth, other than cost
Date posted: November 30, 2021. Answers (1)
- Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system(Solved)
Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system
Date posted: November 30, 2021. Answers (1)
- Define the term node as applied in data transmission(Solved)
Define the term node as applied in data transmission
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
(Solved)
Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
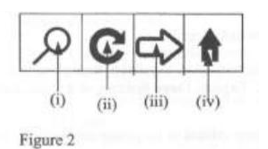
Date posted: November 30, 2021. Answers (1)
- Outline four roles of user agent as used in email software(Solved)
Outline four roles of user agent as used in email software
Date posted: November 30, 2021. Answers (1)
- Describe two modes of licensing for network software(Solved)
Describe two modes of licensing for network software
Date posted: November 30, 2021. Answers (1)
- Figure 1 shows an Ethernet frame. Outline the parts labelled(Solved)
Figure 1 shows an Ethernet frame. Outline the parts labelled
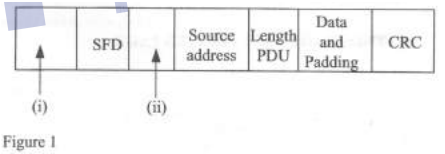
Date posted: November 30, 2021. Answers (1)
- Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks(Solved)
Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks
Date posted: November 30, 2021. Answers (1)
- Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend(Solved)
Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend
Date posted: November 30, 2021. Answers (1)
- Distinguish between channel B and channel D as used in integrated services digital network (ISDN)(Solved)
Distinguish between channel B and channel D as used in integrated services digital network (ISDN)
Date posted: November 30, 2021. Answers (1)
- Outline two applications of a CSMA/CD technology(Solved)
Outline two applications of a CSMA/CD technology
Date posted: November 30, 2021. Answers (1)
- Describe two classification of fiber optic cables(Solved)
Describe two classification of fiber optic cables
Date posted: November 30, 2021. Answers (1)
- TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol...(Solved)
TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol that promotes its reliable transport
Date posted: November 30, 2021. Answers (1)
- Explain three functions of data link layer(Solved)
Explain three functions of data link layer
Date posted: November 30, 2021. Answers (1)
- Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols(Solved)
Routing protocols are critical in data transmission. Explain three functions that likely to be performed by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between symmetric and asymmetric keys as used in network security(Solved)
Differentiate between symmetric and asymmetric keys as used in network security
Date posted: November 30, 2021. Answers (1)