1. Peer-to-peer network operating systems allow users to share network resources saved in a common, accessible network location. In this architecture, all devices are treated equally in terms of functionality. Peer-to-peer usually works best for small to medium LANs and is cheaper to set up.
2. Client/server network operating systems provide users with access to resources through a server. In this architecture, all functions and applications are unified under one file server that can be used to execute individual client actions regardless of physical location. The client/server tends to be most expensive to implement and requires a large amount of technical maintenance. An advantage to the client/server model is that the network is controlled centrally, makes changes or additions to technology easier to incorporate.
Titany answered the question on November 30, 2021 at 11:23
- Explain the following terms as used in the internet
i) add on
ii)URL
(Solved)
Explain the following terms as used in the internet
i) add on
ii)URL
Date posted: November 30, 2021. Answers (1)
- Anne recommended a converged network design for a client. Explain three benefits of the design that could influence the decision(Solved)
Anne recommended a converged network design for a client. Explain three benefits of the design that could influence the decision
Date posted: November 30, 2021. Answers (1)
- John was troubleshooting a computer that was not connecting to network. Outline four possible causes of the problem(Solved)
John was troubleshooting a computer that was not connecting to network. Outline four possible causes of the problem
Date posted: November 30, 2021. Answers (1)
- Outline three factors that should be used when selecting the type of computer network(Solved)
Outline three factors that should be used when selecting the type of computer network
Date posted: November 30, 2021. Answers (1)
- Functions of Intermediary Devices(Solved)
Functions of Intermediary Devices
Date posted: November 30, 2021. Answers (1)
- Distinguish between intermediary and host devices(Solved)
Distinguish between intermediary and host devices
Date posted: November 30, 2021. Answers (1)
- Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation(Solved)
Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation
Date posted: November 30, 2021. Answers (1)
- Outline two factors that should be considered when selecting an Internet bandwidth, other than cost(Solved)
Outline two factors that should be considered when selecting an Internet bandwidth, other than cost
Date posted: November 30, 2021. Answers (1)
- Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system(Solved)
Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system
Date posted: November 30, 2021. Answers (1)
- Define the term node as applied in data transmission(Solved)
Define the term node as applied in data transmission
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
(Solved)
Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
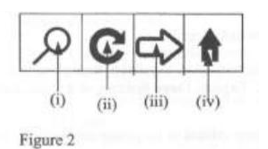
Date posted: November 30, 2021. Answers (1)
- Outline four roles of user agent as used in email software(Solved)
Outline four roles of user agent as used in email software
Date posted: November 30, 2021. Answers (1)
- Describe two modes of licensing for network software(Solved)
Describe two modes of licensing for network software
Date posted: November 30, 2021. Answers (1)
- Figure 1 shows an Ethernet frame. Outline the parts labelled(Solved)
Figure 1 shows an Ethernet frame. Outline the parts labelled
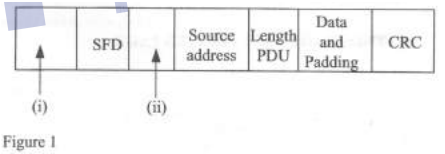
Date posted: November 30, 2021. Answers (1)
- Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks(Solved)
Explain three circumstances that would necessitate the installation of a point-to-point protocol in corporate networks
Date posted: November 30, 2021. Answers (1)
- Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend(Solved)
Cloud computing is widely used in business firms. Explain two benefits that could be influencing the trend
Date posted: November 30, 2021. Answers (1)
- Distinguish between channel B and channel D as used in integrated services digital network (ISDN)(Solved)
Distinguish between channel B and channel D as used in integrated services digital network (ISDN)
Date posted: November 30, 2021. Answers (1)
- Outline two applications of a CSMA/CD technology(Solved)
Outline two applications of a CSMA/CD technology
Date posted: November 30, 2021. Answers (1)
- Describe two classification of fiber optic cables(Solved)
Describe two classification of fiber optic cables
Date posted: November 30, 2021. Answers (1)
- TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol...(Solved)
TCP /IP is known for it capability to provide reliable transportation of data packets from the source to destination. Explain three features of the protocol that promotes its reliable transport
Date posted: November 30, 2021. Answers (1)