
Features
TCP is reliable protocol. That is, the receiver always sends either positive or negative acknowledgement about the data packet to the sender, so that the sender always has bright clue about whether the data packet is reached the destination or it needs to resend it.
TCP ensures that the data reaches intended destination in the same order it was sent.
TCP is connection oriented. TCP requires that connection between two remote points be established before sending actual data.
TCP provides error-checking and recovery mechanism.
TCP provides end-to-end communication.
TCP provides flow control and quality of service.
TCP operates in Client/Server point-to-point mode.
TCP provides full duplex server, i.e. it can perform roles of both receiver and sender.
Details
1) Multi-Vendor Support. TCP/IP is implemented by many hardware and software vendors. It is an industry standard and not limited to any specific vendor.
2) Interoperability. Today we can work in a heterogeneous network (consisting of devices, Operating Systems, software from different vendors) because of TCP/IP. A network user who is using a Windows Operating System based computer can download files from a Linux machine, because both Operating Systems support TCP/IP. TCP/IP eliminates the cross-platform/multi-vendor boundaries.
3) Logical Addressing. Every network adapter has a globally unique and permanent physical address, which is known as MAC address (physical address or hardware address). The physical address is burnt into the card while manufacturing. Low-lying hardware-conscious protocols on a LAN deliver data packets using the adapter's physical address. The network adapter of each computer listens to every transmission on the local network to determine whether a message is addressed to its own physical address.
For a small LAN, this will work well. But when your computer is connected to a big network like internet, it may need to listen to millions of transmissions per second. This may cause your network connection to stop functioning.
To avoid this, network administrators often segment (divide) big networks into smaller networks using devices such as routers to reduce network traffic, so that the unwanted data traffic from one network may not create problem in another network. A network can be again subdivided into smaller subnets so that a message can travel efficiently from its source to the destination. TCP/IP has a robust subnetting capability achieved using logical addressing. A logical address is an address configured through the network software. The logical addressing system used in TCP/IP protocol suite is known as IP address.
4) Routability. A router is a network infrastructure device which can read logical addressing information and direct data across the network to its destination. TCP/IP is a routable protocol, which means the TCP/IP data packets can be moved from one network segment to another.
5) Name Resolution. IP addresses are designed for the computers and it is difficult for humans to remember many IP addresses. TCP/IP allows us to use human-friendly names, which are very easy to remember (Ex. www.omnisecu.com). Name Resolutions servers (DNS Servers) are used to resolve a human readable name (also known as Fully Qualified Domain Names (FQDN)) to an IP address and vice versa.
6) Error Control and Flow Control. The TCP/IP protocol has features that ensure the reliable delivery of data from source computer to the destination computer. TCP (Transmission Control Protocol) defines many of these error-checking, flow-control, and acknowledgement functions.
7) Multiplexing/De-multiplexing. Multiplexing means accepting data from different applications and directing that data to different applications listening on different receiving computers. On the receiving side the data need to be directed to the correct application, for that data was meant for. This is called De-multiplexing. We can run many network applications on the same computer, by using logical channels called ports. TCP/IP provides means for delivering packets to the correct application based on port numbers. In TCP/IP, ports are identified by using TCP or UDP port numbers.
Titany answered the question on November 30, 2021 at 11:37
- ) Copper cables are prone to cross talk. Explain two measures that could be used to mitigate this impairment(Solved)
) Copper cables are prone to cross talk. Explain two measures that could be used to mitigate this impairment
Date posted: November 30, 2021. Answers (1)
- Dina investigated the disadvantages of time-division multiplexing (TDM) in circuit data connection. Explain two disadvantages that she could have established(Solved)
Dina investigated the disadvantages of time-division multiplexing (TDM) in circuit data connection. Explain two disadvantages that she could have established
Date posted: November 30, 2021. Answers (1)
- Distinguish between multicast and broadcast IP addresses(Solved)
Distinguish between multicast and broadcast IP addresses
Date posted: November 30, 2021. Answers (1)
- Outline two parts of to a point point protocol (PPP)(Solved)
Outline two parts of to a point point protocol (PPP)
Date posted: November 30, 2021. Answers (1)
- Explain two characteristics of a Storage Area Network(Solved)
Explain two characteristics of a Storage Area Network
Date posted: November 30, 2021. Answers (1)
- Access Points (AP) are critical in wireless networks. Describe two types of AP that are likely to be used(Solved)
Access Points (AP) are critical in wireless networks. Describe two types of AP that are likely to be used
Date posted: November 30, 2021. Answers (1)
- Computer networks are vulnerable to various types of physical threats. Outline four types of these threats(Solved)
Computer networks are vulnerable to various types of physical threats. Outline four types of these threats
Date posted: November 30, 2021. Answers (1)
- Rene was required to select a network operating system (NOS) for his company’s network. Explain two categories of NOS that he could make his choice(Solved)
Rene was required to select a network operating system (NOS) for his company’s network. Explain two categories of NOS that he could make his choice
Date posted: November 30, 2021. Answers (1)
- Explain the following terms as used in the internet
i) add on
ii)URL
(Solved)
Explain the following terms as used in the internet
i) add on
ii)URL
Date posted: November 30, 2021. Answers (1)
- Anne recommended a converged network design for a client. Explain three benefits of the design that could influence the decision(Solved)
Anne recommended a converged network design for a client. Explain three benefits of the design that could influence the decision
Date posted: November 30, 2021. Answers (1)
- John was troubleshooting a computer that was not connecting to network. Outline four possible causes of the problem(Solved)
John was troubleshooting a computer that was not connecting to network. Outline four possible causes of the problem
Date posted: November 30, 2021. Answers (1)
- Outline three factors that should be used when selecting the type of computer network(Solved)
Outline three factors that should be used when selecting the type of computer network
Date posted: November 30, 2021. Answers (1)
- Functions of Intermediary Devices(Solved)
Functions of Intermediary Devices
Date posted: November 30, 2021. Answers (1)
- Distinguish between intermediary and host devices(Solved)
Distinguish between intermediary and host devices
Date posted: November 30, 2021. Answers (1)
- Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation(Solved)
Explain two circumstances under which unshielded twisted pair (UTP) cables are most applicable in network installation
Date posted: November 30, 2021. Answers (1)
- Outline two factors that should be considered when selecting an Internet bandwidth, other than cost(Solved)
Outline two factors that should be considered when selecting an Internet bandwidth, other than cost
Date posted: November 30, 2021. Answers (1)
- Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system(Solved)
Data communication system should exhibit distinctive features. Explain two desirable features that could be exhibited by the system
Date posted: November 30, 2021. Answers (1)
- Define the term node as applied in data transmission(Solved)
Define the term node as applied in data transmission
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
(Solved)
Figure 2 shows a typical tool bar of a browser program. Outline the functions of
each of the tools labelled (i), (ii), (iii) and (iv)
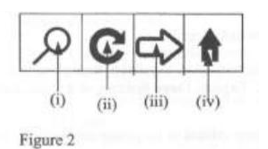
Date posted: November 30, 2021. Answers (1)
- Outline four roles of user agent as used in email software(Solved)
Outline four roles of user agent as used in email software
Date posted: November 30, 2021. Answers (1)