
Contention-based protocol.
Contention-based protocol. A protocol that allows multiple users to share the same spectrum by defining the events that must occur when two or more transmitters attempt to simultaneously access the same channel and establishing rules by which a transmitter provides reasonable opportunities for other transmitters to operate. Such a protocol may consist of procedures for initiating new transmissions, procedures for determining the state of the channel (available or unavailable), and procedures for managing retransmissions in the event of a busy channel. Contention-based protocols shall fall into one of two categories:
(1) An unrestricted contention-based protocol is one which can avoid co-frequency interference with devices using all other types of contention-based protocols.
(2) A restricted contention-based protocol is one that does not qualify as unrestricted.
Contention-based media access control methods do not require mechanisms for tracking whose turn it is to access the media; therefore, they do not have the overhead of controlled access methods. However, the contention-based systems do not scale well under heavy media use. As use and the number of nodes increases, the probability of successful media access without a collision decreases. Additionally, the recovery mechanisms required to correct errors due to these collisions further diminishes the throughput.
Controlled media access
A media access control is a network data transfer policy that determines how data is transmitted between two computer terminals through a network cable. The media access control policy involves sub-layers of the data link layer 2 in the OSI reference model.
The essence of the MAC protocol is to ensure non-collision and eases the transfer of data packets between two computer terminals. A collision takes place when two or more terminals transmit data/information simultaneously. This leads to a breakdown of communication, which can prove costly for organizations that lean heavily on data transmission.
Titany answered the question on November 30, 2021 at 13:15
- Explain two circumstances under which coaxial cables are most applicable in a network installation(Solved)
Explain two circumstances under which coaxial cables are most applicable in a network installation
Date posted: November 30, 2021. Answers (1)
- State four types of Internet connections used in business firms(Solved)
State four types of Internet connections used in business firms
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows typical tools in browser, Outline the function of each of the tools labelled (i), (ii), (iii) and (iv)(Solved)
Figure 2 shows typical tools in browser, Outline the function of each of the tools labelled (i), (ii), (iii) and (iv)
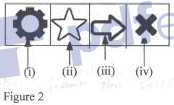
Date posted: November 30, 2021. Answers (1)
- Outline four parts of an email address(Solved)
Outline four parts of an email address
Date posted: November 30, 2021. Answers (1)
- Issues that commonly cause network problems at the physical layer of a network(Solved)
Issues that commonly cause network problems at the physical layer of a network
Date posted: November 30, 2021. Answers (1)
- Common symptoms of network problems at the physical layer (Solved)
Common symptoms of network problems at the physical layer
Date posted: November 30, 2021. Answers (1)
- Describe any three layers of TCP/IP model (Solved)
Describe any three layers of TCP/IP model
Date posted: November 30, 2021. Answers (1)
- Basic Network Troubleshooting Steps(Solved)
Basic Network Troubleshooting Steps
Date posted: November 30, 2021. Answers (1)
- Describe two types of user interfaces in network operating systems(Solved)
Describe two types of user interfaces in network operating systems
Date posted: November 30, 2021. Answers (1)
- Wireless networks are commonly used in business firms. Outline four benefits of the network (Solved)
Wireless networks are commonly used in business firms. Outline four benefits of the network
Date posted: November 30, 2021. Answers (1)
- Use of passwords expiration feature in data communication systems is unpopular. Explain two limitations of this feature (Solved)
Use of passwords expiration feature in data communication systems is unpopular. Explain two limitations of this feature
Date posted: November 30, 2021. Answers (1)
- Joan was requested to patch communication software in her company’s computers. Explain two reasons that could have influenced the request (Solved)
Joan was requested to patch communication software in her company’s computers. Explain two reasons that could have influenced the request
Date posted: November 30, 2021. Answers (1)
- Explain two types of cookies as used in the Internet(Solved)
Explain two types of cookies as used in the Internet
Date posted: November 30, 2021. Answers (1)
- With aid of a diagram, describe TCP handshake(Solved)
With aid of a diagram, describe TCP handshake
Date posted: November 30, 2021. Answers (1)
- Copper cables offer different throughputs in data communication. Outline four factors that influence the cables(Solved)
Copper cables offer different throughputs in data communication. Outline four factors that influence the cables
Date posted: November 30, 2021. Answers (1)
- With the aid of a diagram, describe a time-division multiplexing (TDM)(Solved)
With the aid of a diagram, describe a time-division multiplexing (TDM)
Date posted: November 30, 2021. Answers (1)
- Routing protocols use routing tables to establish the source and destination of data packets in transit. Explain three routing path determination methods used by these...(Solved)
Routing protocols use routing tables to establish the source and destination of data packets in transit. Explain three routing path determination methods used by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between information security and network infrastructure security(Solved)
Differentiate between information security and network infrastructure security
Date posted: November 30, 2021. Answers (1)
- A network design should meet several user needs. Outline four examples of such needs(Solved)
A network design should meet several user needs. Outline four examples of such needs
Date posted: November 30, 2021. Answers (1)
- Explain three advantages of extranet networks in organizations(Solved)
Explain three advantages of extranet networks in organizations
Date posted: November 30, 2021. Answers (1)