 Get premium membership
Get premium membership and access questions with answers, video lessons as well as revision papers.

Functionalities of the Presentation layer
Specific functionalities of the presentation layer are as follows:
1) Translation
• The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bit streams because different computers use different encoding schemes.
• The Presentation layer is responsible for compatibility between these encoding methods.
• The Presentation layer at the sender's side changes the information from its sender dependent format.
• The Presentation layer at the receiving machine changes the common format into its receiver’s dependent format.
Example: Convert ASCII code to EBCDIC code.
2) Encryption
• The system must be able to assure privacy regarding the message or information as it also carries sensitive information.
• Encryption means that the sender transforms the original information or message to another form, this data after encryption is known as the ciphertext and this ciphertext sends the resulting message out over the network.
• Decryption concerned with the transform of the message back to its original form. This decrypted data is known as plain text.
3) Compression
• Data Compression means reduces the number of bits to be transmitted by this reduce the bandwidth of the data.
• Data Compression becomes particularly important in the transmission of multimedia such as audio, video, text, etc.
Titany answered the question on November 30, 2021 at 13:16
- Difference between contention-based and controlled media access methods(Solved)
Difference between contention-based and controlled media access methods
Date posted: November 30, 2021. Answers (1)
- Explain two circumstances under which coaxial cables are most applicable in a network installation(Solved)
Explain two circumstances under which coaxial cables are most applicable in a network installation
Date posted: November 30, 2021. Answers (1)
- State four types of Internet connections used in business firms(Solved)
State four types of Internet connections used in business firms
Date posted: November 30, 2021. Answers (1)
- Figure 2 shows typical tools in browser, Outline the function of each of the tools labelled (i), (ii), (iii) and (iv)(Solved)
Figure 2 shows typical tools in browser, Outline the function of each of the tools labelled (i), (ii), (iii) and (iv)
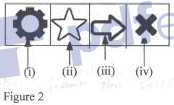
Date posted: November 30, 2021. Answers (1)
- Outline four parts of an email address(Solved)
Outline four parts of an email address
Date posted: November 30, 2021. Answers (1)
- Issues that commonly cause network problems at the physical layer of a network(Solved)
Issues that commonly cause network problems at the physical layer of a network
Date posted: November 30, 2021. Answers (1)
- Common symptoms of network problems at the physical layer (Solved)
Common symptoms of network problems at the physical layer
Date posted: November 30, 2021. Answers (1)
- Describe any three layers of TCP/IP model (Solved)
Describe any three layers of TCP/IP model
Date posted: November 30, 2021. Answers (1)
- Basic Network Troubleshooting Steps(Solved)
Basic Network Troubleshooting Steps
Date posted: November 30, 2021. Answers (1)
- Describe two types of user interfaces in network operating systems(Solved)
Describe two types of user interfaces in network operating systems
Date posted: November 30, 2021. Answers (1)
- Wireless networks are commonly used in business firms. Outline four benefits of the network (Solved)
Wireless networks are commonly used in business firms. Outline four benefits of the network
Date posted: November 30, 2021. Answers (1)
- Use of passwords expiration feature in data communication systems is unpopular. Explain two limitations of this feature (Solved)
Use of passwords expiration feature in data communication systems is unpopular. Explain two limitations of this feature
Date posted: November 30, 2021. Answers (1)
- Joan was requested to patch communication software in her company’s computers. Explain two reasons that could have influenced the request (Solved)
Joan was requested to patch communication software in her company’s computers. Explain two reasons that could have influenced the request
Date posted: November 30, 2021. Answers (1)
- Explain two types of cookies as used in the Internet(Solved)
Explain two types of cookies as used in the Internet
Date posted: November 30, 2021. Answers (1)
- With aid of a diagram, describe TCP handshake(Solved)
With aid of a diagram, describe TCP handshake
Date posted: November 30, 2021. Answers (1)
- Copper cables offer different throughputs in data communication. Outline four factors that influence the cables(Solved)
Copper cables offer different throughputs in data communication. Outline four factors that influence the cables
Date posted: November 30, 2021. Answers (1)
- With the aid of a diagram, describe a time-division multiplexing (TDM)(Solved)
With the aid of a diagram, describe a time-division multiplexing (TDM)
Date posted: November 30, 2021. Answers (1)
- Routing protocols use routing tables to establish the source and destination of data packets in transit. Explain three routing path determination methods used by these...(Solved)
Routing protocols use routing tables to establish the source and destination of data packets in transit. Explain three routing path determination methods used by these protocols
Date posted: November 30, 2021. Answers (1)
- Differentiate between information security and network infrastructure security(Solved)
Differentiate between information security and network infrastructure security
Date posted: November 30, 2021. Answers (1)
- A network design should meet several user needs. Outline four examples of such needs(Solved)
A network design should meet several user needs. Outline four examples of such needs
Date posted: November 30, 2021. Answers (1)