1. CRAMM (CCTA Risk Analysis and Management Method)
It was created in 1987 by the Central Computing and Telecommunications Agency (CCTA), now renamed into Office of Government Commerce (OGC), of the United Kingdom government. CRAMM is currently on its fifth version, CRAMM Version 5.0. It comprises three stages, each supported by objective questionnaires and guidelines. The first two stages identify and analyze the risks to the system. The third stage recommends how these risks should be managed. Although it is developed for use in information security it is highly applicable in any other form of security. The three stages of CRAMM are as follows:
Stage1. The establishment of the objectives for security by:
• Defining the boundary for the study
• Identifying and valuing the physical assets that form part of the system
• Determining the ‘value’ of the object of security by interviewing users about the potential impacts that could arise from unavailability, destruction, disclosure or modification
• Identifying and valuing the security assets that form part of the system.
Stage 2 The assessment of the risks to the proposed system and the requirements for security by:
• Identifying and assessing the type and level of threats
• Assessing the extent of vulnerabilities to the identified threats
• Combining threat and vulnerability assessments with asset values to calculate measures of risks.
Stage 3 Identification and selection of countermeasures that are commensurate with the measures of risks calculated in Stage 2. CRAMM contains a very large countermeasure library consisting of over 3000 detailed countermeasures organized into over 70 logical groupings.
2. MEHARI (Method for Harmonized Analysis of Risk)
It is an information risk analysis assessment and risk management method developed and distributed by CLUSIF (French association of information security professionals). As well it is applicable in many security contexts. MEHARI 2010 allows a flexible use of the following elements:
i. Threat analysis: top business managers describe their activities and list the potential dysfunctions having an impact on the organization's activity and values are given to the business impact.
ii. List the organizational, human and technical assets contributing to their realization, this allows to create cartography of the assets. This is done by analyzing the organization business.
iii. The assets (services and data) used by these activities are given a classification level according to three classic security criteria (confidentiality, integrity, availability) plus the necessary efficiency regarding compliance to laws and regulations (like protection of personal information or of the environment),
iv. The intrinsic likelihood of representative threat event types is considered.
3. Quantitative analysis
This is based on the quantitative definitions of risk as grounded in statistics theory to give statistical estimates. Often, the probability of a negative event is estimated using the frequency of past similar events or by event tree methods, but probabilities for rare failures may be difficult to estimate if an event tree cannot be formulated. This makes risk assessment difficult in hazardous industries, for example nuclear energy, where the frequency of failures is rare and harmful consequences of failure are numerous and severe. In statistics, the notion of risk is often modeled as the product of an undesirable outcome. This combines the probabilities of various possible events and some assessment of the corresponding harm into a single value. The simplest case is a binary possibility of Accident or No accident. The associated formula for calculating risk is then:
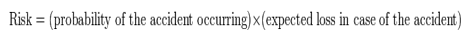
For example, if performing activity X has a probability of 0.01 of suffering an accident of A, with a loss of 1000, and then total risk is a loss of 10, the product of 0.01 and 1000.
In a situation with several possible accidents, total risk is the sum of the risks for each different accident, provided that the outcomes are comparable:

For example, if performing activity X has a probability of 0.01 of suffering an accident of A, with a loss of 1000, and a probability of 0.000001 of suffering an accident of type B, with a loss of 2,000,000, then total loss expectancy is 12, which is equal to a loss of 10 from an accident of type A and 2 from an accident of type B.
4. Fear as intuitive risk assessment
People rely on their fear and hesitation to keep them out of the most profoundly unknown circumstances. True fear is a gift. It is a survival signal that sounds only in the presence of danger. The challenge is that unwarranted fear largely controls human beings. Risk could be said to be the way we collectively measure and share the "true fear"—a fusion of rational doubt, irrational fear, and a set of UN quantified biases from our own experience. Recognizing and respecting the irrational influences on human decision making may do much to reduce disasters caused by naive risk assessments that presume to rationality but in fact merely fuse many shared biases.
Titany answered the question on
December 7, 2021 at 07:17