- A computer user is unable to retrieve a file stored in a server in organization.
State three reasons why the user will need to contact the...(Solved)
A computer user is unable to retrieve a file stored in a server in organization.
State three reasons why the user will need to contact the network administrator.
Date posted: November 14, 2019.
- Explain the following terms as used in desktop publishing.(Solved)
Explain the following terms as used in desktop publishing.
a. Embedded object.
b. Autoflow.
Date posted: November 14, 2019.
- The formula =$M30+Q$20 was typed in cell R15 and then copied to cell M24 of a spreadsheet. Write the formula as it appears in cell...(Solved)
The formula =$M30+Q$20 was typed in cell R15 and then copied to cell M24 of a spreadsheet. Write the formula as it appears in cell M24.
Date posted: November 14, 2019.
- Give any two characteristics of master file.(Solved)
Give any two characteristics of master file.
Date posted: November 8, 2019.
- Perform the following binary arithmetic.(Solved)
Perform the following binary arithmetic.


Date posted: November 8, 2019.
- Give any two benefit of hacking to an organization’s computer system.(Solved)
Give any two benefit of hacking to an organization’s computer system.
Date posted: November 8, 2019.
- Mention any three ways of ensuring efficient back up of data.(Solved)
Mention any three ways of ensuring efficient back up of data.
Date posted: November 8, 2019.
- List three paragraph formatting features of word processors.(Solved)
List three paragraph formatting features of word processors.
Date posted: November 8, 2019.
- Briefly explain the following terms as used in spreadsheet.
(i) Cell
(ii) Range
(iii) Value
(iv) Function(Solved)
Briefly explain the following terms as used in spreadsheet.
(i) Cell
(ii) Range
(iii) Value
(iv) Function
Date posted: November 8, 2019.
- State two operational methods of an organizational ensuring the security of data.(Solved)
State two operational methods of an organizational ensuring the security of data.
Date posted: November 8, 2019.
- Study the following pseudocode and answer the questions that follow.(Solved)
Study the following pseudocode and answer the questions that follow.
 i. Determine the value of N and X.
ii. Draw a flowchart of the above pseudocode.
i. Determine the value of N and X.
ii. Draw a flowchart of the above pseudocode.
Date posted: November 8, 2019.
- Explain how you would change the name of a worksheet in Microsoft Excel.(Solved)
Explain how you would change the name of a worksheet in Microsoft Excel.
Date posted: November 8, 2019.
- Explain the meaning of the following terms as used in computer data transmission.(Solved)
Explain the meaning of the following terms as used in computer data transmission.
(a) Simplex transmission
(b) Half duplex transmission
(c) Full duplex transmission
Date posted: November 8, 2019.
- Explain any two ways in which computers have been made user-friendly for persons that are physically challenged.(Solved)
Explain any two ways in which computers have been made user-friendly for persons that are physically challenged.
Date posted: November 8, 2019.
- State any two types of documentation created in system development.(Solved)
State any two types of documentation created in system development.
Date posted: November 8, 2019.
- Anthony, a student at Kericho Technical College defined a computer as "an electronic device which accepts, processes data and produce information depending on its decisions"....(Solved)
Anthony, a student at Kericho Technical College defined a computer as "an electronic device which accepts, processes data and produce information depending on its decisions". Was this student right? Explain you answer.
Date posted: November 8, 2019.
- Work out 3210-1910 in 8-bit binary notation;(Solved)
Work out 3210-1910 in 8-bit binary notation;
(i) As a signed magnitude representation using ones complements.
(ii) Using two’s complement
Date posted: November 7, 2019.
- Convert each of the following numbers;(Solved)
Convert each of the following numbers;
(i) 126810 to hexadecimal
(ii) 51C3D16 to its binary equivalent
(iii) 84C16 to octal
(iv) 1768 to hexadecimal.
Date posted: November 7, 2019.
- State and explain two reasons why higher number systems were developed in computing(Solved)
State and explain two reasons why higher number systems were developed in computing
Date posted: November 7, 2019.
- The information in figure 3 below is maintained by the patron of wildlife club in a school. Study it and answer the questions that follow.(Solved)
The information in figure 3 below is maintained by the patron of wildlife club in a school. Study it and answer the questions that follow.
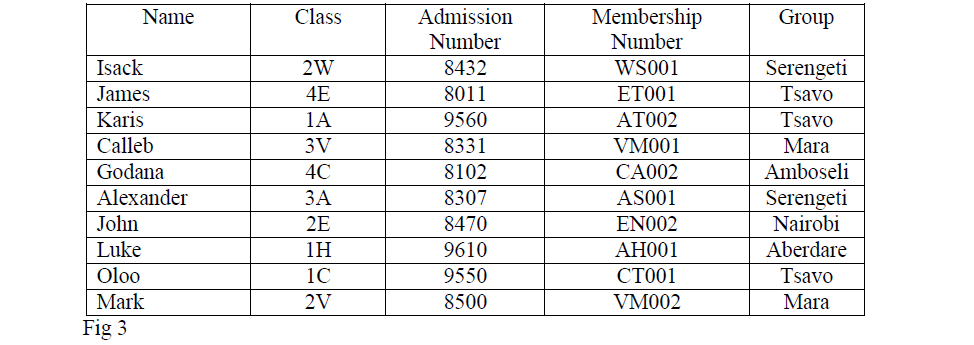 (a) Describe the field values, records and file.
(b) State the most appropriate primary key for the list.
(c)State the most appropriate data types for the fields:
(i) Admission number
(ii) Membership number.
(d) If a database was to be created for the list; forms, tables, queries and reports are likely to be used.
(i) State the purpose of each of these objects.
(ii) Which objects cannot be used to store the data in the list?
(e) (i) How many field values are in the list?
(ii) How many records are in the list?
(a) Describe the field values, records and file.
(b) State the most appropriate primary key for the list.
(c)State the most appropriate data types for the fields:
(i) Admission number
(ii) Membership number.
(d) If a database was to be created for the list; forms, tables, queries and reports are likely to be used.
(i) State the purpose of each of these objects.
(ii) Which objects cannot be used to store the data in the list?
(e) (i) How many field values are in the list?
(ii) How many records are in the list?
Date posted: November 7, 2019.
- An airline uses an information system whereby if a passenger at station A books a plane seat, this transaction is immediately shown at stations A...(Solved)
An airline uses an information system whereby if a passenger at station A books a plane seat, this transaction is immediately shown at stations A and B such that no other passenger can book the same seat.
(I) Name this data processing mode.
(II) State two advantages of this data processing mode.
Date posted: November 7, 2019.
- State two advantages of using coaxial cables over satellite in data communication.(Solved)
State two advantages of using coaxial cables over satellite in data communication.
Date posted: November 7, 2019.
- Define the term data communication.(Solved)
Define the term data communication.
Date posted: November 7, 2019.
- What is meant by Blog?(Solved)
What is meant by Blog?
Date posted: November 7, 2019.
- Study the flowchart in figure 2 below and use it to answer the questions that follow.(Solved)
Study the flowchart in figure 2 below and use it to answer the questions that follow.
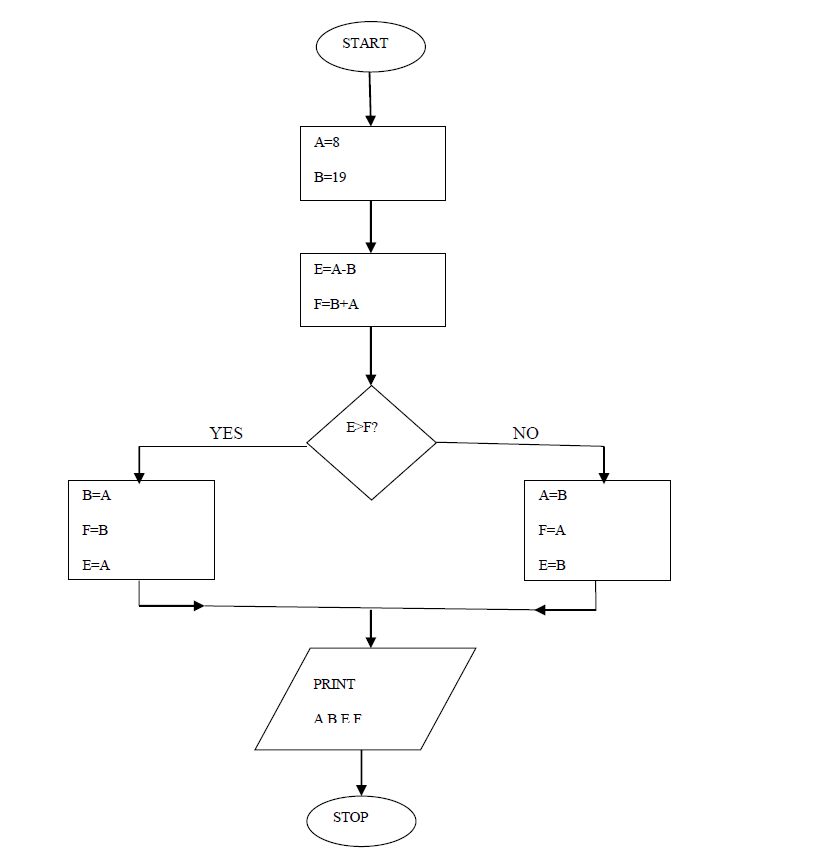 (i) Name the control structures used in the flowchart.
(ii) Determine the value of A, B, C and F.
iii) Write a pseudocode for the flowchart in figure above.
(i) Name the control structures used in the flowchart.
(ii) Determine the value of A, B, C and F.
iii) Write a pseudocode for the flowchart in figure above.
Date posted: November 7, 2019.
- List two factors that dictate the cost of a computer system.(Solved)
List two factors that dictate the cost of a computer system.
Date posted: November 7, 2019.
- Describe the process of transactions handling at the electronic point of sale terminals in a retail outlet(Solved)
Describe the process of transactions handling at the electronic point of sale terminals in a retail outlet
Date posted: November 7, 2019.
- What are repetitive strain injuries?(Solved)
What are repetitive strain injuries?
Date posted: November 7, 2019.
- A trader uses a spreadsheet program to calculate profits.
The figure below shows the spreadsheet.(Solved)
A trader uses a spreadsheet program to calculate profits.
The figure below shows the spreadsheet.
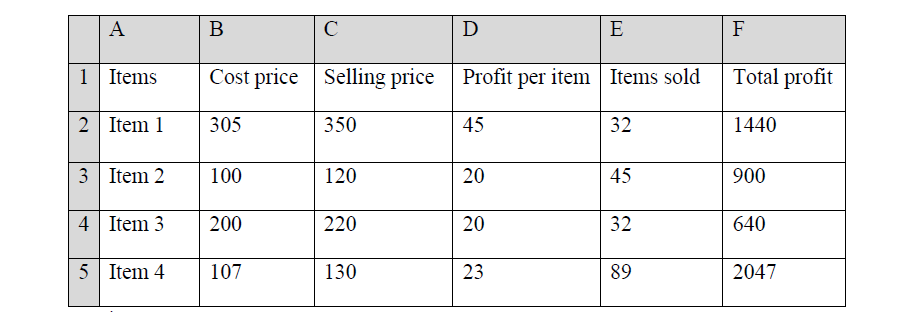 (a)Which row contains labels only?
(b) Write the formula that has been entered in cell F2.
(a)Which row contains labels only?
(b) Write the formula that has been entered in cell F2.
Date posted: November 7, 2019.
- Give three hardware considerations that should be made before installing an operating system.(Solved)
Give three hardware considerations that should be made before installing an operating system.
Date posted: November 7, 2019.